The Department of Homeland Security (DHS) and SecureLogix Team on TDoS Research
Jul 5, 2015 •
For those following my blog, you know that Telephony Denial of Service (TDoS) is a flood of unwanted inbound calls, typically to an enterprise contact center. The calls can arrive at any enterprise or any part of an enterprise, but are normally targeted at critical voice lines. This includes 911, other public safety numbers, hospital emergency rooms and intensive care units, key parts of financial contact centers, and other organizations. TDoS attacks are the most significant form of voice-related DoS, because they involve malicious calls, are easy to generate, and can affect enterprises using both TDM and SIP networks. The following diagram illustrates a TDoS attack:
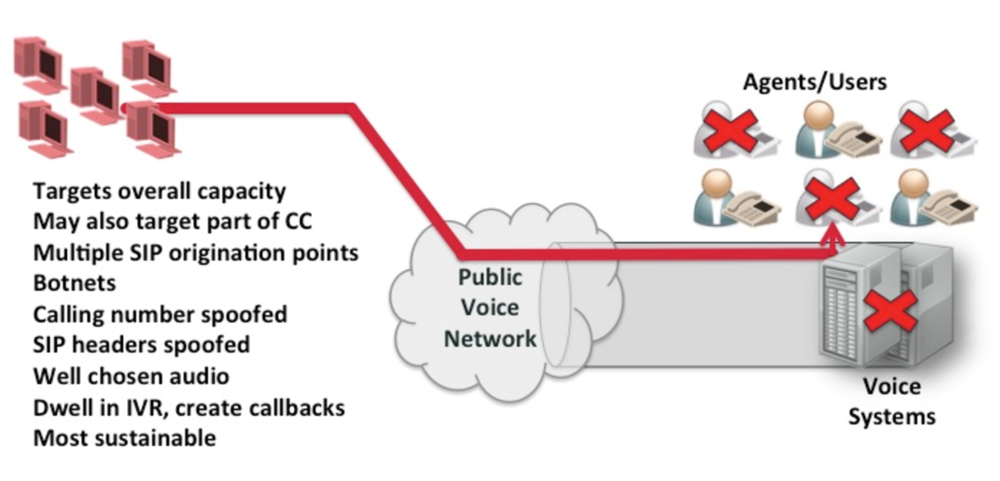
The Department of Homeland Security (DHS), the Federal Bureau of Investigation (FBI), and service providers have produced a number of warnings and bulletins about TDoS. A few of the more recent ones can be found in prior posts on this blog.
There have been over 1000 attacks reported to service providers and the Department of Homeland Security (DHS). A good summary can be found at https://nakedsecurity.sophos.com/2014/01/22/tdos-extortionists-jam-phone-lines-of-public-services-including-hospitals/.
Attacks such as this are simple, but still very effective. They do not involve a significant amount of volume in terms of concurrent calls and they are not very sophisticated or complex in terms of spoofing call information, such as the calling party number or ANI. We expect that in the near term, more complex attacks will be seen, involving greater sophistication in terms of spoofing call information and much greater volume. The following table illustrates the progression we have seen and expect in the future for TDoS:
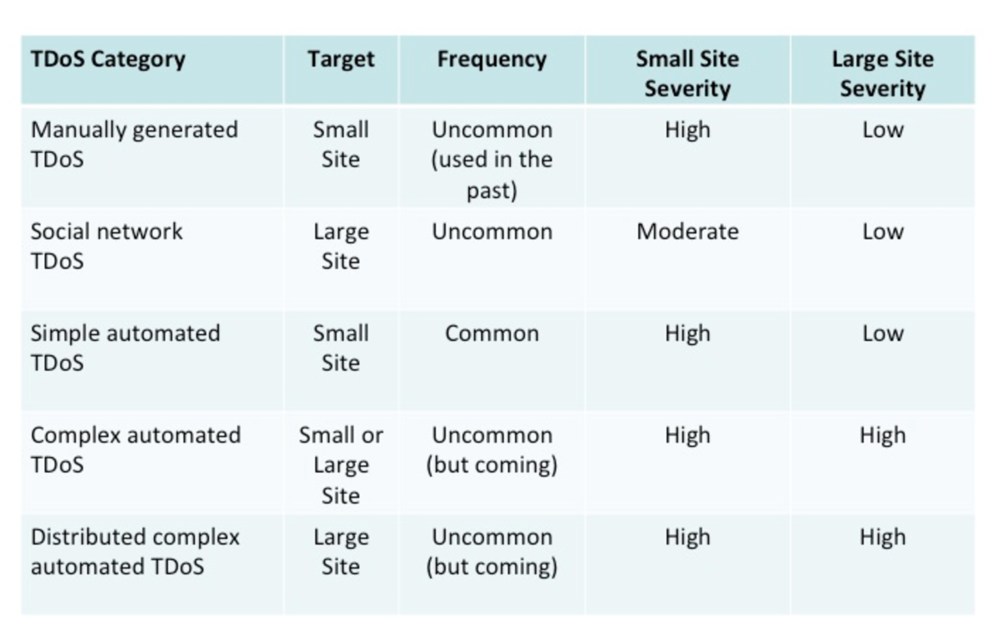
In a short amount of time, we expect these attacks to become more common, be more sophisticated (complex), and involve greater volume (distributed). This will make the attacks much more difficult to detect and mitigate, both for the target enterprise as well as service providers.
The DHS Science and Technology Directorate (S&T) Cyber Security Division (CSD) recognizes the TDoS threat and has funded SecureLogix for two Research and Development (R&D) efforts. The first effort is to define the evolving threat, define enterprise and service provider countermeasures, and build solutions for these environments. The second effort involves a broad look at security issues affecting Next Generation 911, including TDoS, which will be particularly disruptive for these environments. These R&D efforts will produce a TDoS solution that can address the most sophisticated attacks, for both TDM and SIP networks, within both enterprise and service provider networks. While the final solution is still being developed, a basic approach involves use of several filters, which score calls based upon pre-call signaling information, queries to network authentication services, and then content and possible use of turing tests. All controlled by enterprise-defined policy. These filters are shown in the following diagram:
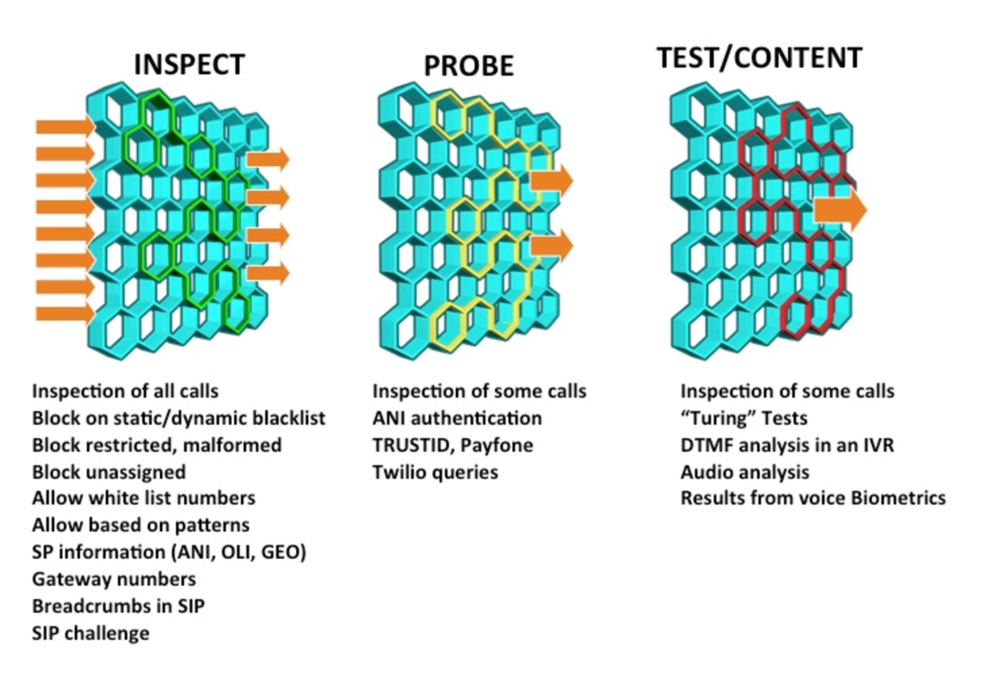
We will be posting more information as this R&D effort progresses. You can track our progress on these efforts by following this blog and our twitter feeds at @markcollier46 and @dhsscitech.

